Happy Spring! The flowers are in bloom, the pollen is falling from the trees, and the phish are swimming upstream. Today I am presenting to you a quick paper on a recent phishing attack directed at our corporate email account. As this is the exact type of attack I am seeing with all of our clients, I thought it useful to give you a little walkthrough of my basic analysis, to help you in preventing an attack like this becoming a significant breach of your organization, or personal, data.
Initial Email #
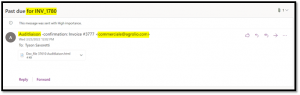
Take a look the above email. This is a straightforward phish with some obvious red flags:
- “Your money or your life” The phishing email alerts to a past-due amount (uh oh!)
- Company name not formatted correctly (Should be Audit Liaison)
- Numerical conflict (is it Invoice 1780, or 3777?)
- Unrecognized vendor domain (it’s an olive oil company, check it out! com)
- Downloadable attachment (we’ll take a closer look at this!)
Technical Control Check #
You very likely are using an email service (Google, Outlook, etc.) that performs some perfunctory technical analysis of domains and attempts to authenticate the sender of the email. If an email is obviously spoofed, or comes from a known, untrustworthy domain, it will be blocked. In our case today, the olive oil company Agrolio.com appears to have been compromised and is now being used to facilitate this credential harvesting attack. Since the olive oil company seems to exist, and isn’t on some CIA blacklist, our email servers don’t know it is being used for malicious intent. You could, after all, being buying olive oil like any normal human being.
This gets a little technical, but if we are looking at the headers of the email (the nerdy stuff that most of us are comfortable never dealing with), we see that our email service attempted to authenticate this email.
It passed the checks, detected no spoofing or weird redirects, and allowed this phishing email to reach our inbox; right next to my typical EVOO emails.
Checking Contents of Attached Files #
What about that file that was attached to the phishing email? You can ignore the file name, as that is often used to try and trick you. If you look at the extension (the information to the right of the “.”), you’ll see that it is an .html file. This is essentially a “web page” file, and opening it use your browser to browse…somewhere. It isn’t safe to just go to any website that a file directs you, so I did basic analysis by opening the file in a text editor (Notepad++ in this case).
What you see below indicates that this file is attempting to run a script from another source. Long story short, this script will make it appear that you are trying to log on to a Microsoft account (spoiler alert, this is the attack). I have highlighted in yellow a key piece of the script.
You can see that my email “was” listed here before I edited it. In order to safely access this script, I opened a test environment and edited the script to an email that looks similar to, but is different from, my real email address (it says Tyson.savoretti@auditliaisonTEST.com instead of Tyson.savoretti@auditliaison.com) If this script does what I think it does, we will see my TEST address show up instead of my real one.
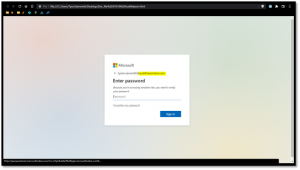
Fake Login Page #
So now we double-click the link and the script is launched (don’t try this at home). What we see now is a FAKE authentication/login page, opened from my computer and includes the TEST email address we modified in the original script. If you were to type your password into the password field, you can probably guess what happens next…You’d be sending your password to the bad guy, without him ever even having to go through the trouble of guessing it.
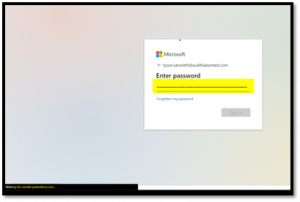
Sending Your Password to the Bad Guys #
I typed a password to see what happens next. I obviously wanted to troll the hacker a bit so I actually sent 300MBs worth of random text through the password field. This hacker didn’t seem to sanitize his fields so maybe I broke his database (here’s hoping). In the below screen we can see that when we click the “Sign In” button, the information gets sent to sender.petanitest.com
CONCLUSION #
I looked a few steps deeper and it seems like this hacker has set up a very basic database server to collect the passwords that people send to him. He will likely then attempt to access these email accounts, and any other accounts that make sense, as people often reuse passwords in other systems.
Thank you for taking the time to read this quick report. If you have any questions, please reach out to me or my team. We are passionate about helping our clients and we don’t want you to fall for this intermediate-level phishing attack.
Tyson A Savoretti CISSP, CISA, CEH, ECIH, SSCP, PCI-ISA, PenTest+, CySA+